Key Benefits
Allocate resources efficiently by focusing on critical assets and vulnerabilities that pose the greatest threat.
Better decision-making by evaluating the potential risks and impact of security threats.
Early identification of potential threats and vulnerabilities, enables organizations to implement preventive measures faster.
Meet regulatory cybersecurity requirements by identifying and addressing risks that align with compliance standards.
How It Works
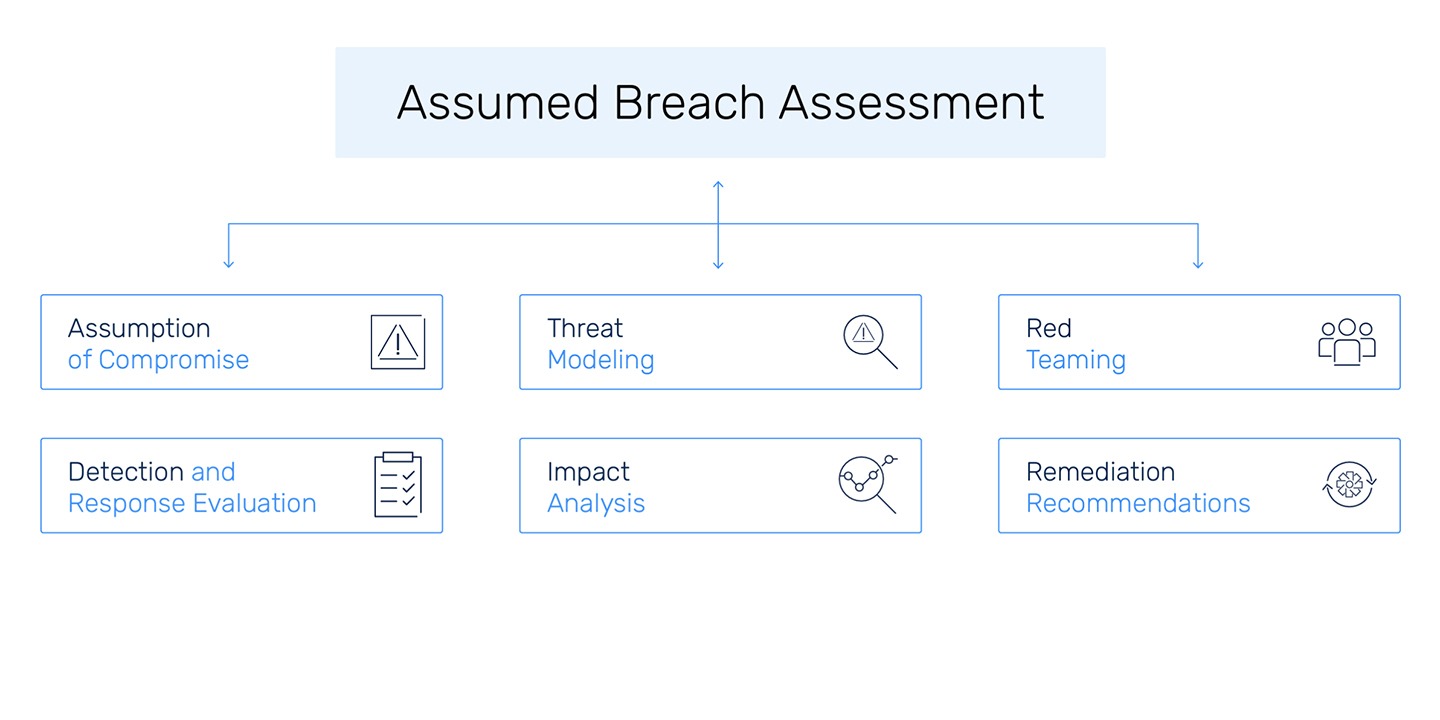
What Does Assumed Breach Assessment Do?
An Assumed Breach Assessment (ABA) is a cybersecurity evaluation approach that operates under the premise that a data breach has already occurred or that attackers have already infiltrated the organization’s network.
What the Solution Delivers
To evaluate the risk posed by potential malicious insiders and assess the effectiveness of controls against internal threats.
Simulate actions of a rogue employee, such as unauthorized access to sensitive systems, data exfiltration, or privilege escalation.
Insights into potential internal security breaches, strategies to improve access controls, monitoring of sensitive operations, and employee risk management.
Benefits of Assumed Breach Assessment
Encourages organizations to think like attackers, which can lead to robust security measures.
Enhances the organization’s ability to respond to real incidents by identifying weaknesses in current processes.
Organizations identify potential threats and vulnerabilities that could be exploited by attackers. This involves understanding the attack surface and possible tactics, techniques, and procedures (TTPs) used by malicious actors.
Help meet regulatory requirements and reduce overall risk exposure by addressing vulnerabilities before they can be exploited.
The assessment examines existing detection and response capabilities, evaluating how well the organization can identify a breach, respond to it, and recover from it.
Based on the findings, the assessment provides recommendations for improving security controls, incident response plans, and overall resilience against future breaches.

How SHQ is Different
Our ABAs include red teaming exercises, where a group of ethical hackers simulate an attack on the organization to identify weaknesses and test the effectiveness of security controls.
Analyzing the potential impact of a breach helps organizations prioritize their security measures. Understanding the consequences of various types of data being compromised informs risk management decisions.
SHQ Response Platform enhances collaboration in pre-empting, identifying, and mitigating risks before they become security incidents.
Need 24/7/365 Assumed Breach
Assessment for your organization?
"*" indicates required fields